PonyFinal Ransomware Sample Download
PonyFinal is a Java based ransomware that is deployed in human operated ransomware attacks. While Java based ransomware are not unheard of, they are not as common as other threat file types. However, organizations should focus less on this payload and more on how it's delivered. Attackers using PonyFinal gain access through brute-force attacks on the systems management server of the target company. They deploy VBScript to run PowerShell back shell, deploy a remote manipulator system to bypass event logging, and in some cases, implement the Java Runtime Environment.
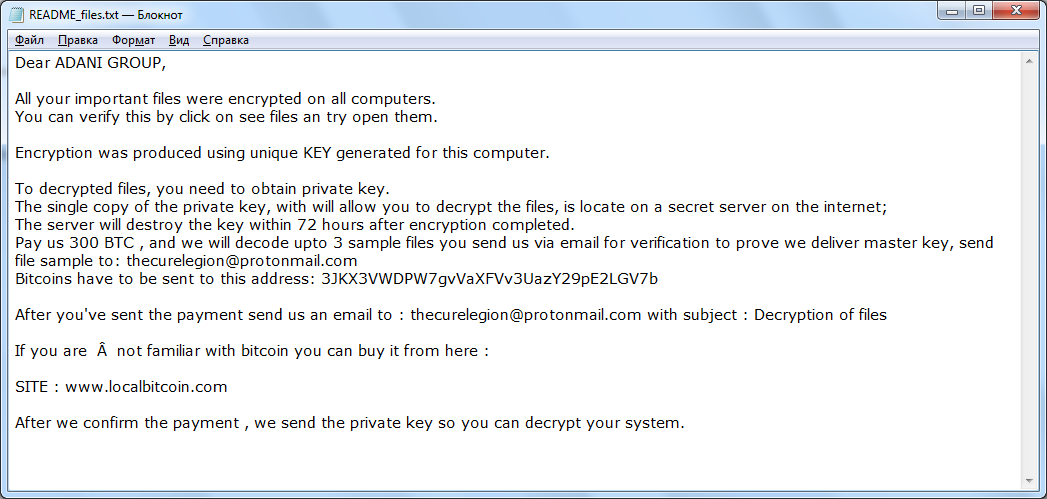
PonyFinal is delivered through an MSI file that contains two batch files and a ransomware payload. UVNC_Install.bat creates a scheduled task called "Java Updater" and calls RunTask.bat, which launches the PonyFinal.JAR payload. This is the tail end of protracted human-operated ransomware campaigns that are known to stay dormant and wait for the most opportune time to deploy the payload. PonyFinal demanded 300 BTC as ransom amount to this address 3JKX3VWDPW7gvVaXFVv3UazY29pE2LGV7b. It appends .enc to its encrypted files.


PonyFinal Ransomware Signatures
Family: Trojan:Java/Infostealer!MSR MD5: e94b18674b8336461c12a2ed48541956 SHA256: 18894db26ee6eff366a81d924b7f4c8e510d98793b307638e67721da15eaebba
PonyFinal Ransomware Download

Click to Load Comments
