MedusaLocker Ransomware Sample Download
MedusaLocker Ransomware encrypts user data using AES + RSA-2048, and then requires victim to be sent an email to purchase the decryption program. The project file says: MedusaLocker.pdb. A "Medusa" section is also created in the registry. There are several variants of MedusaLocker but there functionality is same. Only difference is the file extensions which can be .encrypted .bomber .boroff .breakingbad .locker16 .newlock .nlocker .skynet. Most of its features are of a typical Ransomware but MedusaLocker can encrypt the contents of mapped network drives that may be present on infected systems. It manipulates Windows functionality to force network drives to be remapped so that their contents can also be encrypted and it can uses ICMP sweeping to profile the network to identify other systems that can be used to maximize the likelihood of a ransom payment.
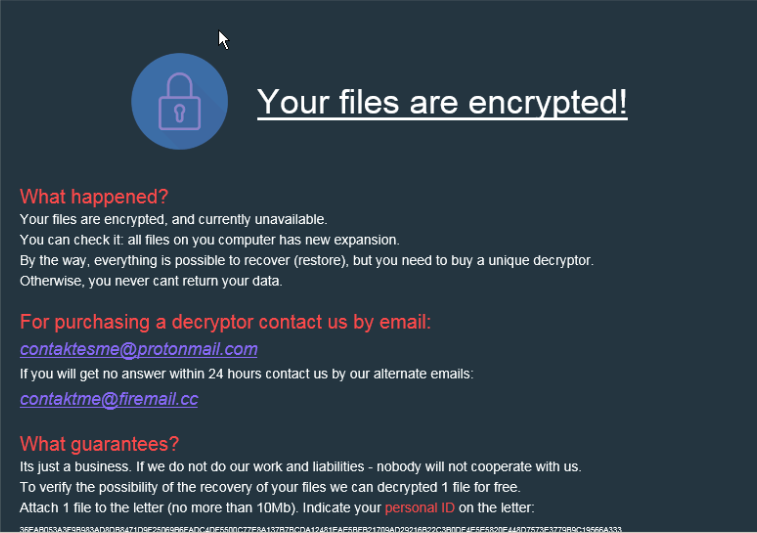


MedusaLocker Ransomware Signatures
Family: Ransom:Win32/Ako!MSR MD5: 19ddac9782acd73f66c5fe040e86ddee SHA256: dde3c98b6a370fb8d1785f3134a76cb465cd663db20dffe011da57a4de37aa95
MedusaLocker Ransomware Download

Click to Load Comments

