Loda RAT Malware Sample Download
Loda RAT, first detected in 2017 which now slowly matures up into an effective remote access Trojan, yet simple. It steal username/passwords, session cookies and can take screenshots too. Its current version in wild is 1.1.1. Infection process is simple, it started with a phishing e-mail with Microsoft Word document as attachment.
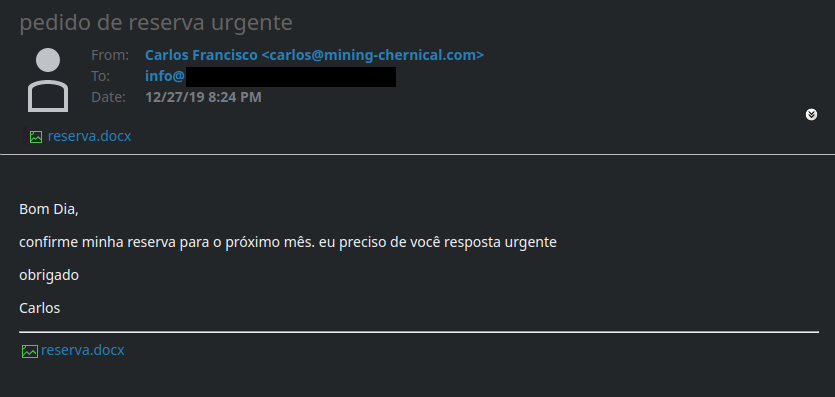
The document is obfuscated which hide it from AV detection. Once the document is opened a MSI file is downloaded and executed which smuggle data from victim machine to it Command and Control server.


The document is obfuscated which hide it from AV detection. Once the document is opened a MSI file is downloaded and executed which smuggle data from victim machine to it Command and Control server.
Loda RAT Document Signatures
Family: Trojan:Script/Woreflint.A!ctv MD5: a624ef9b0920caf8c255c15a2e09ad43 SHA256: b5df816986a73e890f41ff0c0470a2208df523f17eb4eac9c5f0546da2ec161e
Loda RAT Document Download

Loda RAT MSI Signatures
Family: Trojan:Win32/Occamy.C MD5: 2e2074810be6b6167f1dc288cf9def7b SHA256: 9edd2bfdb0c177f046cec1392d31ee3f67174e0a23fdf7e4b6fd580e769f0493
Loda RAT MSI Download

Click to Load Comments


